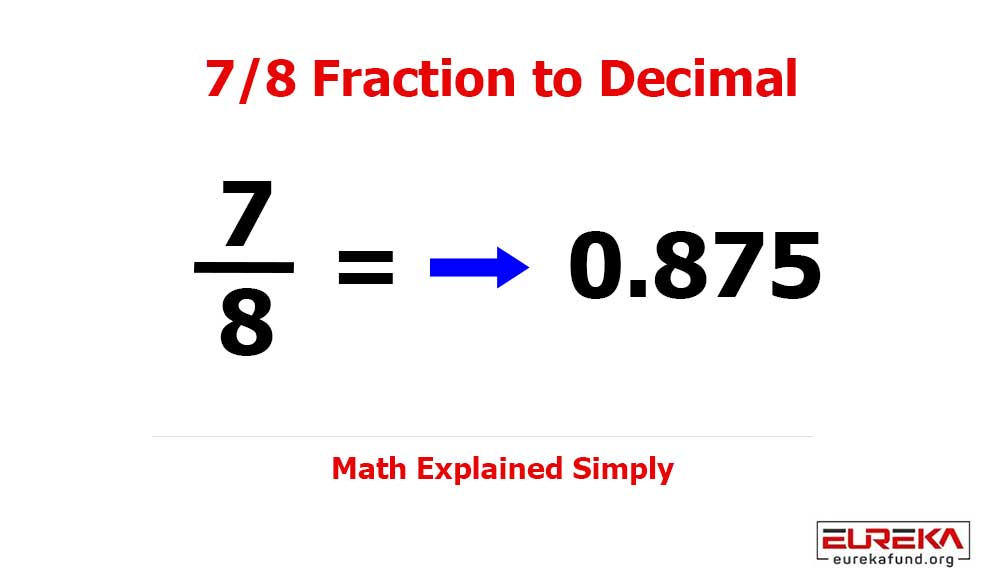
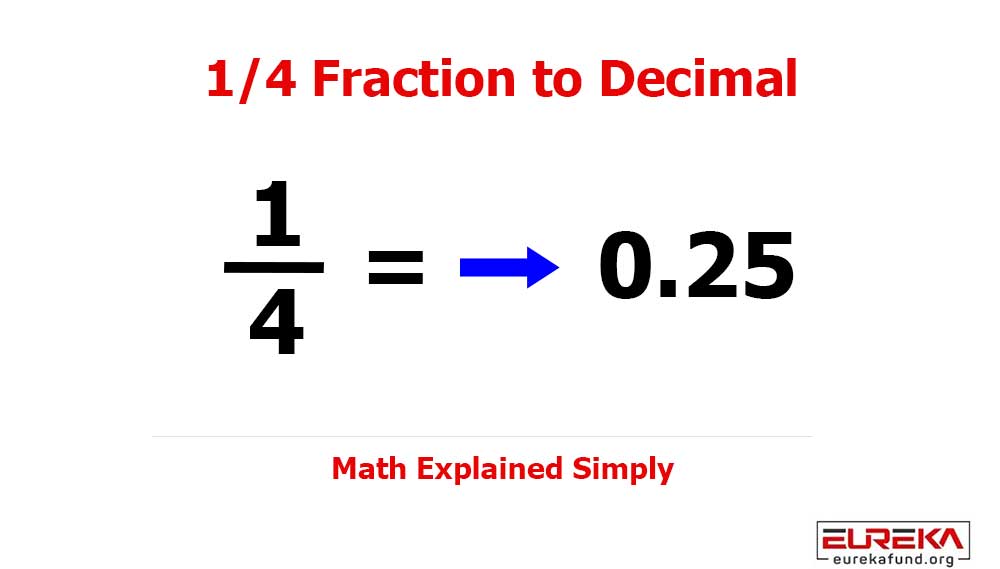
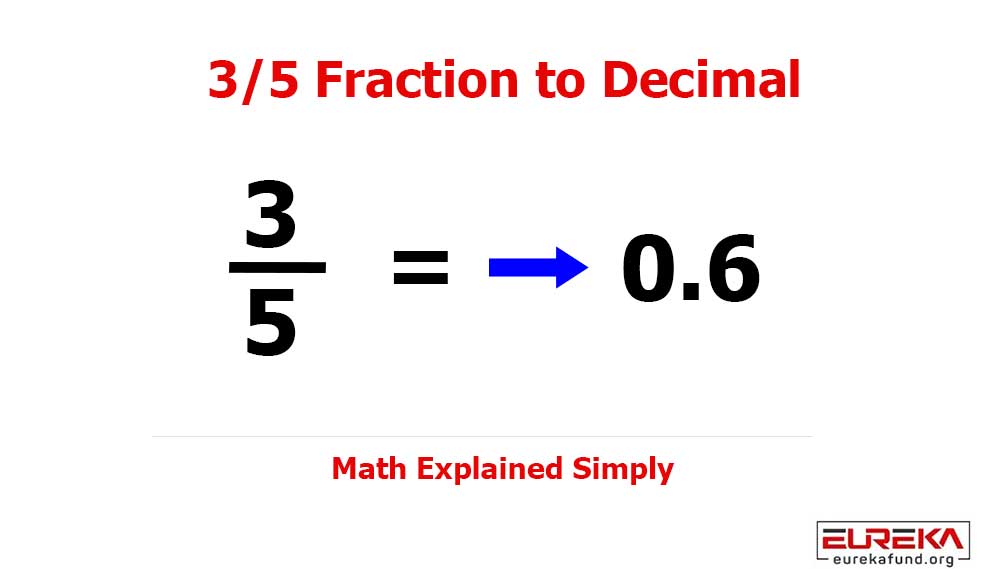
In an age where our lives are increasingly intertwined with the digital realm, safeguarding sensitive information has never been more critical. From personal photos to financial records, data protection is essential.
This article will explore the fundamental elements of a robust data protection strategy. Whether you’re an individual or a business owner, understanding these key components is crucial in the fight against cyber threats and data breaches. Let’s dive into data security to ensure your digital life remains safe and secure.
1. Data Encryption: Shielding Information from Prying Eyes
Data encryption is like putting your data in a secure vault with a complex lock. It involves converting your data into a code you can only unlock with the correct key. It ensures that even if unauthorized individuals gain access to your data, it remains unreadable and useless to them.
Using robust encryption methods is fundamental to your digital security concerns. Encryption should be applied to data in transit (e.g., during online transactions) and data at rest (e.g., on your computer or server).
2. Access Control: Limiting Data Access to Authorized Users
Controlling who can access your data is crucial. Access control involves setting up permissions and restrictions to ensure only authorized individuals can view, edit, or delete specific data. It is typically done through the following:
- User authentication
- Passwords
- Role-based access
Limiting access to only those who need it reduces the risk of insider threats and accidental data leaks.
3. Regular Data Backups: Preparing for the Worst
Imagine your data is like a fragile glass sculpture. Accidents can happen; sometimes, data can be lost or corrupted due to hardware failures, human errors, or cyberattacks.
Regular data backups are your safety net. By creating duplicate copies of your data and storing them in secure locations, you can quickly recover lost information and minimize downtime in case of a disaster.
4. Security Awareness Training: Educating Your First Line of Defense
The weakest link in any data protection strategy is often the people interacting with the data daily. It includes employees who may unknowingly fall victim to phishing scams or fail to follow security protocols.

Security awareness training is essential. It educates individuals about the risks, best practices, and their role in data protection. Teaching them to recognize suspicious emails or websites, use strong passwords, and follow security guidelines can reduce the likelihood of security breaches.
5. Incident Response Plan: Being Prepared for the Unexpected
No matter how robust your security measures are, there’s always a chance that a breach or incident could occur. That’s where an incident response plan comes in. It’s like a fire drill for data security. It outlines the steps to take when a data breach is detected, including who to contact, how to contain it, and how to communicate with affected parties.
In addition, engaging with an IT service provider like Terminal B is vital to assist in handling the breach effectively. A well-defined plan can minimize the damage caused by a breach and help your organization recover more quickly.
Create a Successful Data Protection Strategy
A strong data protection strategy is like a shield that safeguards your information from cyber threats. By focusing on encryption, access control, regular backups, security training, and having an incident response plan, you can create a robust defense against data breaches.
Protecting data is an ongoing commitment in our digital world, ensuring your valuable information stays safe and secure.